“Knowledge Must be Free”, so it is freely provided many Windows Tricks / Tips and free Softwares for educational purposes and self-practice only. However, you should agree to Disclaimer & Agreements mentioned herein. Moreover, all the materials here, are really hard works of mine or someone else, you should appreciate & respect these hard works.
Wednesday, April 30, 2008
Total Training - Adobe Fireworks CS3

Web Services Security

Web Services are appearing and dominate as new application solutions. At the same time they present great challenges for security. This book describes a union of Web Services and information security. Several technologies are presented (i.e. XML Signature, XML Encryption, SAML...), and then related to Web Services so that the reader can get the whole picture. The book consists of five parts and each of them is dedicated to one topic. The first part is, as expected, entitled Introduction. The authors present web services, security, and some new challenges as well as new threats. As an introduction to Web Services Security they define web services as applications that can be described, published, located, and invoked over a network. Here you find an introduction to XML as a quite verbose language.Speaking about security, some building blocks of security are presented: confidentiality, authentication, authorization, integrity, non-repudiation, privacy, and availability.
Full Metal Jacket
Rapidshare
Principles of Protocol Design

Rapidshare
Password: knowfree.net
What does mdash mean?

mdash can be represented numerically using &# 150; in HTML, or '\u2014' in Java.
ndash can be represented numerically using &# 150; in HTML, or '\u2013' in Java.
It's All in Your Head: Thinking Your Way to Happiness

Here are the simple truths that motivate people of any age to find and accept lasting happiness, illustrated with the stories of real people, and illuminated with the observations of spiritual leaders and great philosophers.For more than three decades, attorney, financial consultant, and life coach Stephen M. Pollan has been advising clients and readers on the business of living everything from home buying and employment contracts to marriage and parenting. He has taught his clients and readers to Die Broke (use assets rather than build up an estate), to stage Second Acts (reinvent their lives), and, most recently, to Fire Your Boss (take charge of their own work lives).
Rapidshare
Tuesday, April 29, 2008
How to Remove Linux from Your PC Safely and Restore your MBR

So HFS Partitions are not seen by windows, so its hidden.
To remove the partitions of Linux in WindowsXP go to your 'Control panel' > Admistrative Tools > Computer Managment.
Open 'Disk Management' and you will see your Linux drives recognised as 'Unknown Partition' plus the status of the drive. Bearing in mind you know what partition and disk you installed to it will be easier to recognise as the drive/partition where you had installed it to.
Once you have followed this through, you will now have free space.
This next part is very important. Once you have formatted the drive, re format it as your required file system type. either Fat32 or NTFS. Now the important part is coming up !
Have a Windows Boot disk with all the basic DOS Commands loaded on to the disk. A standard Windows 98/Me Boot Disk will work too.
Type in the DOS command :
e.g, from your C:\
fdisk /mbr
Or use your Windows XP run the recovery console, pick which xp install you would like to boot in to (usually you will pick #1)
then type: fixmbr. Answer Y to the dialoge.
Your master boot record will now be restored and Windows XP will be bootable once again. Your System will be restored with your original boot loader that you got with Windows XP.
Paypal Hacks: 100 Industrial Strength Tips And Tools

Download Link:
Rapidshare
VTC - Adobe Illustrator CS3

Network Convergence: Services Applications Transport and Operations Support

What is Zero Filling?
- Zero filling is a way to overwrite all data on a hard drive. An analogy would be putting new asphalt over an old highway. This snip is from the Seagate Website: "(Quick) will write over the beginning of the drive which includes the critical partition information, eliminating all partitions and information on the drive including the Master boot record. This is useful if you have a drive that has a corrupted partition or that you wish to erase to reinstalll a fresh operating system and new data. (Full) will write over the entire data area of the drive. This is useful if a drive has bad sectors that cannot be fixed by the operating system. This will also erase all the data on the drive, but it will take several hours."
- The simplest way to think of zero filling is setting every single byte of a storage device (RAM, HDD, whatever it may be), to null (character code 0). This effectively cleans the device of any data. This full text is online at: http://www.seagate.com/support/kb/disc/faq/ ata_llfmt_what. html
- Zero filling removes the data on a HD 100%. This is especially useful in preventing data being stolen from your HD. After doing a zero filling, (apparently) no tool can retrive data from your HD and everything is permanently deleted.
- Zero filling is a low level hard disk management technique. As it suggests, it "fills the hard disk with zeros". By that, I mean that it magnetically prepares the disk to be a fresh disk, consisting of only zeros, no ones.
- There is another common definition for 'Zero filling'. Typically, in software development you will have numeric entry fields where significant digits are important. If those digits are not entered you will 'zero fill' them to ensure the entire value is filled. For example, if you have a field which is six long and enter '123' then you will zero fill to get a value of '000123'.
Linux Complete Command Reference

Rapidshare
Password: www. itakate.net
Monday, April 28, 2008
Microsoft Access 2007 Data Analysis

Data analysis is the process of categorizing data into groups, translating large amounts of data into meaningful information, and performing a wide variety of calculations in a fraction of the time it would normally take by hand. Showing readers how to save time and increase productivity, this unique book explains how to analyze data using the latest version of Micro$oft Access, the world's leading PC database system. Practical, real-world scenarios demonstrate the benefits of using Access for data analysis, show how to avoid common pitfalls of everyday data crunching, and illustrate the differences and similarities between Access and Excel data analysis.
Rapidshare
Upgrading and Repairing Microsoft Windows

Ultrauploading
Learning Autodesk Maya: Lighting

What are the Different Types of Booting?
1]. A "cold boot" or a "hard reset," which occurrs when the computer (or micro processor system) is powered-up. The system has no history from the previous time it run, and needs to perform comprehensive initialization.
2]. A "warm boot" or "soft reset," which occurrs when resetting the computer or micro processor system without interrupting its power supply. The continued supply of power allows certain initialization tasks to be skipped in the reboot, compared to the cold boot, and the re-initialization might complete sooner.
As part of every boot process, the computer will typically load and initialize an operating system. Subject to the type of computer and operating system, this system might be sourced from mass-storage media such as hard drives, floppy diskettes or DVDs, from networked media such as a network server, or from build-in memory devices such as read-only memory (ROM). Some operating systems may take advantage of reduced initialization during a warm boot, but this is not typically the case with modern mainstream general-purpose computing operating systems.
Windows Vista Bible, Desktop Edition

Check out the best of Windows Vista in this handy desktop-size resource. This convenient reference is drawn from the very best of bestselling author Alan Simpson's Alan Simpson's Windows Vista Bible. You'll discover how to master the basics of PCs and operating systems, get started on Vista, and move ahead to multimedia, adding security, building a network, and more. You'll even find special tips, workarounds, and advice on how to deal with Vista's quirkier aspects.
Rapidshare
Sunday, April 27, 2008
Guitar Man
04. Jerry's Breakdown
Download Link:
Rapidshare
How can make Unlimited Downloads from Megaupload
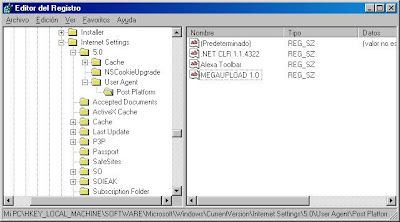
2]. Click on Run Option
3]. Type regedit and press on OK
4]. Goto: HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows\ CurrentVersion\ Internet Settings.0\ User Agent\ Post Platform
5]. Add a new Alphanumeric key (REG_SZ) and type MEGAUPLOAD 1.0
6]. Reboot the Internet Explorer
Hacking the Cable Modem

Download Link:
Rapidshare
How to Develop a Super Power Memory

Download Link:
Rapidshare or Easy-Share
Lynda.com - Aperture 2 New Features

Security for Wireless AD HOC Networks

The objective of this book is to make the readers aware of the fundamentals of the area of security of wireless networks as well as the open problems. This will hopefully spur much more activity in this area in the upcoming years. This book provides a broad and comprehensive overview of the research that has been done to date on the security of wireless ad hoc networks and discusses the advantages and disadvantages of the various schemes that have been proposed in the literature. This book will be of interest to a wide variety of people. A beginner in the field will benefit from a simple description of the various problems and solutions. Such a person will also gain by having a ready compendium of important results in this area thereby saving such a person from the problem of information overload. Thus, this book can be used as a textbook in the first class focusing on security in ad hoc networks.
What is the Best Operating System and Why?
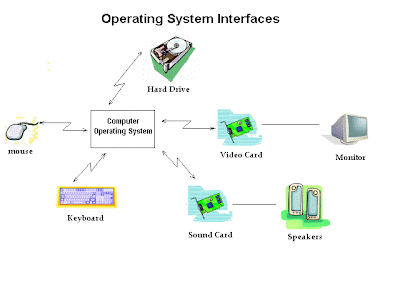
The best operating system to use depends on what its intended use will be and who will be using it. There is no specific operating system which can be called "the best" overall, and since most current operating systems share most common and advanced features there is much debate on the topic. A few of the most popular operating system, their pros and cons, and some of their best uses are described below.
Microsoft Windows
Pros:
- The largest library of programs and applications.
- Some commercial games work only with Windows and DirectX.
- Almost all hardware has drivers which are compatible with Windows.
- Most widely used.
Cons:
- Prone to viruses, spyware, and adware if proper steps not taken such as installation of internet security software, which reduces performance speed.
- Requires regular maintenance to avoid system errors and reduced performance.
- Even with maintenance, issues can slowly accumulate requiring a re-installation of Windows to restore performance and fix software issues.
- Expensive.
- Windows Vista has high system requirements.
- The Windows market share has seen some decrease in recent years and months.
- Does not support multiple desktop workspaces unlike Mac OS X and Linux.
Notes:
- Windows Vista, the most recent consumer version of Windows, has relatively high system requirements compared to its Windows XP and other operating systems. There are also other issues, such as some software and hardware incompatibilities or frequent security confirmations, which are causing many individuals and businesses to continue using the older Windows XP.
- The two most common versions of Windows are Windows XP and Windows Vista. Vista, although it has some issues, does have some new features such as search-as-you-type search and a 3D-accelerated desktop, features up until now only found in Mac OS X and some versions of Linux.
- With the introduction of Virtual-machine software, Windows has become a popular add-on for Mac and Linux in order allow those computers to support Windows-only software or hardware when needed.
Best uses:
- Gamers
- People who must use Windows-only software for work or school.
- People or businesses looking for an inexpensive computer yet do not have the ability to use Linux.
- Relatively simple and intuitive interface with many advanced features.
- Not virus or malware prone: there are no Mac OS X viruses in the wild, and with its UNIX base, it is fairly resilient. There are a small number of trojans (malicious software) which have been known to take effect through applications running in Mac OS X, though they are almost always found on illegal-content-based websites and are not of significant concern.
- Second-largest selection of software, with many high-quality Mac-only programs in existence, such as those found in iLife. Although at one point software for certain tasks were not mac-compatible, all software is now either Mac-compatible or has an equivalent that is. Most advanced games have also recently became compatible with Mac OS X.
- Reliable and high performance.
Cons:
- Limited to Apple-manufactured hardware.
- Some hardware does not have Mac-compatible drivers, though the number of this hardware has recently become small and negligible.
- It can be difficult to do certain cross-platform network hardware sharing for a Mac OS X based computer in a Windows network or visa-versa. For example, a printer's Mac driver may not support cross-platform printing to a Windows-connected printer, and replacement drivers may or may not exist.
Notes:
- There are some security holes in Mac OS X just like in other operating systems, and, like in other operating systems, they are fixed with occasional updates upon their discovery. However, Mac OS X includes a built-in firewall, and hacks aimed at Mac are less common than hacks aimed at Windows, so this is not generally a major concern.
- Macs are usually more expensive than PCs made by companies such as Dell and HP. However, the following factors can cause the total price of owning a Mac to be less than that of a PC: Mac OS X and Apple iWork are relatively inexpensive compared to copies of Microsoft Windows or Microsoft Office. PCs experience hardware or software failures more frequently than Macs, increasing service and replacement costs.
- With a relatively low market share compared to Windows, there are still individual programs which are only Windows compatible. However, virtual machine software with a Windows installation or compatibility layer software can allow those programs to run even on a Mac.
- The Mac has seen significant market share increases in recent years and months, something which has also increased the amount of Mac-compatible software.
Best uses:
- Students who are not required to use Windows-specific software (though Windows can easily be installed to use Windows software). A recent study indicated that the number of students intending to purchase Macs has neared that of Windows-based PCs.
- Home users looking for an easy and reliable computing experience who are willing to pay more than typical PC prices.
- Graphic designers and photographers.
- Scientists.
Pros:
- Low number of virsues and spyware, similar to Mac OS X
- Usually free
- Large number of types of Linux to choose from.
- Has a large amount of free and open source software equivalents to commercial Windows and Mac software
- More easily customizable
- Can run many Windows programs with the use of a compatibility layer such as Wine. (Programs such as Cedega can be used to run many Windows games)
- Reliable with good performance and low requirements.
Cons:
- Advanced use and installation of some software may require more advanced knowledge than is required for use of Windows and Mac.
- Many commercial programs do not support Linux
- Small commercial game library
Notes:
- Through customization and software like Beryl, Linux can be made to have advanced desktop effects similar to Aero on Windows Vista or Aqua on Mac OS X.
- "Dependency hell" can make installation of certain programs difficult even for advanced users.
Best uses:
- Experienced computer users looking for a good, free operating system.
- Businesses looking for reliable and affordable computing, so long as they do not need Windows-only software and have a competent IT manager.
Though there is no one clear best operating system, each does have its advantages and disadvantages, and different people will be best using different ones. Microsoft Windows is the most common operating system and is a reasonable choice for most people. Mac OS X is second-most popular (and gaining market share) and is an excellent operating system for those who can purchase a Mac. Linux is very good and advanced operating system available for free and is recommended for experienced users.
Saturday, April 26, 2008
How to Convert File System, FAT/FAT32 to NTFS
Open a dos prompt and give the command
The type "convert d: /fs:ntfs"
This command would convert your d: drive to NTFS.
If the system cannot lock the drive, you will be prompted to convert it during next reboot.
Normally you should select yes.
Conversion from FAT/FAT32 to NTFS is non-destructive, your data on the drive will NOT be lost.
Power Up Your Mind: Learn Faster, Work Smarter

From one of the leading international experts on life-long learning, Power Up Your Mind will revolutionize our understanding of how our brains are pre-wired to learn and the practical steps we can take to prepare ourselves (emotionally and physically) to participate fully in the process. Diagnostic tools, activities, and stories demonstrate the power of esteem, confidence, and motivation on effective learning, describe the role creativity, aging, and emotional readiness play in the learning process, and help readers create a personal action plan for life-long learning.
Rapidshare
The Giant Black Book of Computer Viruses

Software Cinema - Adobe Photoshop Advanced Masking Techniques

Download Link:
Rapidshare_Part_1 / Rapidshare_Part_2
Rapidshare_Part_3 / Rapidshare_Part_4
Rapidshare_Part_5 / Rapidshare_Part_6
Rapidshare_Part_7
Password: www.greek-fun.com
Solar House: A Guide for the Solar Designer

Covering the full life span of the project, from siting issues through specific design features to maintenance of the property and equipment, this is a comprehensive guide to designing, planning and building a solar house.The author uses his experience of living in a solar house to inform the reader of the technology and practices needed for the design, operation and maintenance of the solar home. Each of the technologies of the house, such as space heating and cooling, domestic hot water and electric power technologies, are critiqued from the point of view of the owner/resident, with the author using his thirty years experience of living in a solar home. This provides home owners who are thinking of going solar with first hand evidence of best practice, and provides the architect and designer with the knowledge of how to best satisfy their clients needs.
Rapidshare
Why Does a Computer Suddenly Slow Down?

- Your computer is infected with a virus.
- Your hard-disk is fragmented.
- Your do not have sufficient RAM memory.
- Your windows registry contains many invalid entries.
- Your comp is infected with a spyware.
- Your system files may have become corrupt.
- You are running a lot of programs.
- Running Games and other programs simultaneously.
- Running cad based graphics program with other programs.
- Your hard disk isnt formmated properly.
- Your hard disk may contain bad sector.
- Detection of newly pluged devices.
- Using operating system with high UI on low end system.
- Using programs which are not recommended for your system.
- Type of partion that you use as ur windows partition (Ntfs or Fat32).
Microsoft Expression Web 2 on Demand

Download Link:
Ultrauploading
Thursday, April 24, 2008
Secrets of a Super Hacker

Wednesday, April 23, 2008
Total Training - Microsoft ASP.NET AJAX

Game Design, Second Edition

Lynda.com - ActionScript 3.0: Working with XML

Password: www.darkwarez.pl
Hackers Black Book

The book gives a very good overview of what kind of attacks users are subject when connected to the net. Allot of the people i see on here haven't been able to even get the book to begin with. However I recived the book, and I was dissappointed, greatly. After months of trying to learn about the subject to see if i wanted to progress beyond just programming, and this book gave me very little to work with as far as learning anything, so in short, go get a real book about network hacking to see what they do.
Rapidshare
How to Change the Location of the IE7 Toolbar
1]. Open your favorite registry editor.
2]. Navigate to the following key: HKEY_CURRENT_USER \ Software \ Microsoft \ Internet Explorer \ Toolbar \ WebBrowser
3]. Right click an empty space in the right pane and then click New DWORD Value.
4]. Name the new value ITBAR7Position.
5]. Double click the new value and set the Data Value to 1.
6]. Click OK and close the registry editor.
7]. Close and reopen IE7.This switches the toolbar position for the currently logged on user. If you want to change it back, you can do so by following these same steps and setting the DataValue to 0.
English Vocabulary in Use

Download Link:
Rapidshare
The Extreme Searcher’s Internet Handbook

A phenomenal resource for both extreme and not-so-extreme researchers. Great tips, clear explanations, and years of expertise distilled into 250 pages of clear, engaging text. This book should be on every searcher's desk. Mary Ellen Bates, coauthor, Researching Online for Dummies. Hock has established an enviable reputation for his series of books about search engines and online searching. They are always detailed, insightful, and up to date. This book continues that tradition of excellence. Online Information Review clear and useful guide will help anyone interested in going beyond Google, explaining when, why, and how best to use various search tools and other Web resources.
Rapidshare
Tuesday, April 22, 2008
Lynda.com - Secrets to Selling and Publishing Photography

How to Prepare for any Disaster

Astronomy with a Home Computer

Rapidshare
Video2Brain - Real Life Photoshop Workflows

Award-winning photographers and digital artists show professional workflows with Adobe Photoshop and Wacom Intuos3 Pen TabletProfessional workflows impressive resultsFive internationally successful photographers and digital artists present their work for clients like Carlsberg, Harley-Davidson, DHL or Volkswagen and demonstrate their creative process from the initial image to final digital result. The experts explain their individual configuration of the Wacom pen tablet and show how working with the Wacom Intuos3 pen tablet accelerates retouching and image manipulation in Adobe Photoshop.
Wireless Communications The Future

Password:knowfree. net
How to Customise Your Start Button
Step 1:
1] Run "Resource Hacker" and open the file "%windir%\Explorer.exe".
2] You see a Tree of all Resources in this file, expand the "String Table"
3] Find the "start" and replace it with your own text. then press the [Compile Script] button.
4] Save "Explorer.exe" as "MyStart.exe" DONT save it as Explorer.exe, do "save as.." and give it a new name.
5] Quit "Resource Hacker".
Step 2:
1] Click on the [Start] button and choose the "Run..." item from the start menu. (Or use the shortcut key WinKey+R)
2] Type "RegEdit" in the Run "Dialog Box". And then press the [Ok] buton to run the "Registry Editor" program.
3] Go to:
4] Quit "Registry Editor".
5] Restart your system.
Note about Registry Editor:if you did not find the key
Monday, April 21, 2008
Understanding Windows CardSpace

Rapidshare
Better Than Bullet Points

Rapidshare
VTC - Maya Fundamentals

Download Link:
Rapidshare_Part_1
Rapidshare_Part_2
Sunday, April 20, 2008
Ultimativen Disco Hits

01. Dr. Alban - It's My Life
02. Dan Hartman - Relight My Fire
03. The Weather Girls - It's Raining Men
04. Earth, Wind & Fire - September
05. Alcazar - Crying at the Discoteque
06. Tom Novy Feat. Lima - Now or Never
07. Eiffel 65 - Blue (Da Da Bee)
08. A Touch of Glass - Around the World (La La La)
09. Culture Beat - Mr. Vain
10. Prezioso Feat. Marvin - Tell Me Why
11. Wolfgang Petry - Die Laengste Single Der Welt
12. Modern Talking - You're My Heart, You're My Soul
13. Las Ketchup - the Ketchup Song (Aserej)
14. Lou Bega - Mambo No. 5 (A Little Bit of..)
15. Roland Kaiser - Hit-Mix
16. Dr. Alban - Sing Hallelujah !
How to copy Songs from your iPod to your PC

1]. Connect the iPod to your PC. If iTunes starts syncing (ie erasing) your music automatically, hit the X in the upper right hand corner of iTunes display, to the left of the search box, to stop it.
2]. In Control Panel, Portable Media Devices, double-click your iPod.
3]. Navigate to the Music folder.
4]. Select all the music folders, and drag and drop them into a folder on your hard drive, or directly into iTunes.
And you're done! The iPod music folder structure is strange and inexplicable, but once you move your files into iTunes you can set it to automatically organize your folder by artist and album to clean that up. (To do this, in iTunes Edit menu, choose Preferences and in the Advanced tab, check "Keep iTunes Music Folder organized.")
If you give this a go, lemme know how it goes. I'll ammend the instructions with any additional info for other versions of Windows and iPods.